Introduction
The security of your infrastructure is crucial in the modern digital environment, where cloud computing has become the foundation of many enterprises. You may manage user access to your AWS resources with the help of Amazon Web Services (AWS) powerful Identity and Access Management (IAM) tool. We'll go into the realm of AWS IAM in this blog, looking at its fundamental ideas, recommended procedures, and how it helps create a safe cloud environment.
Understanding AWS IAM
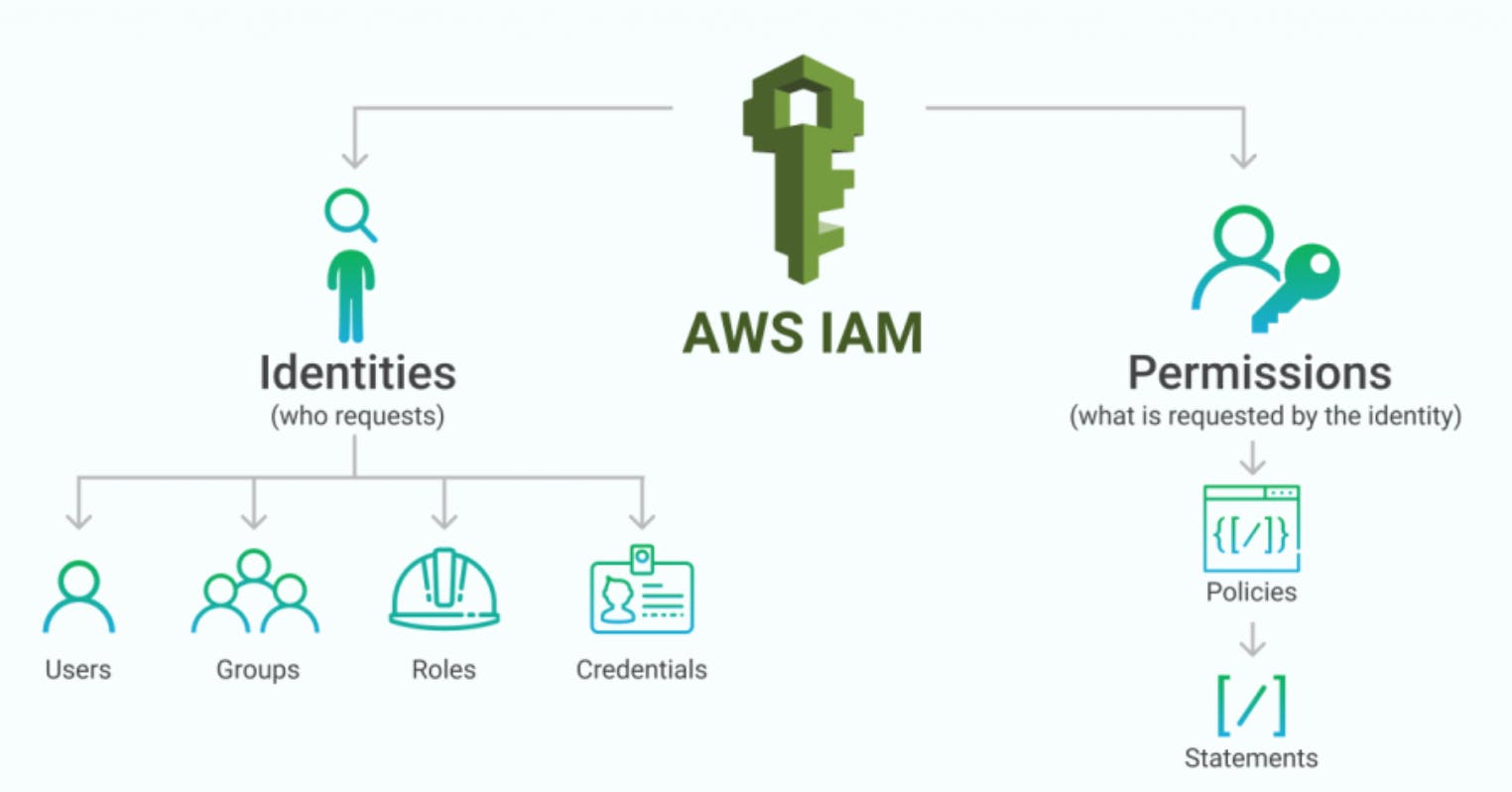
You may securely manage access to AWS resources using the web service known as AWS Identity and Access Management (IAM). It offers a centralized method of handling authentication and authorization, making sure that only approved users or systems can access your AWS infrastructure. IAM operates according to the least privilege principle, providing users and services only the rights necessary to carry out their duties.
Core Concepts of AWS IAM
Users - IAM users are entities that have linked permanent credentials. They might stand in for people or organizations that need access to AWS resources. It is possible to establish, monitor, and grant or remove permissions for users as needed.
Groups - IAM groups are assemblages of IAM users. You can specify permissions at the group level and add or delete individuals as necessary rather than defining rights for each user individually. This makes management easier and guarantees that all users have consistent access.
Roles - IAM roles are comparable to users, but they are not linked to a particular identity. Entities like EC2 instances and AWS services accept roles, which provide them with temporary credentials to access resources. By removing the need to save permanent credentials on instances or apps, roles improve security.
Policies - IAM rules specify permissions and specify the activities that individuals, groups, or roles may do in relation to certain resources. JSON-formatted policies can be applied to individuals, groups, roles, or resources directly.
Best Practices for AWS IAM
Apply the concept of least privilege - Only provide users and services the access they require to complete the tasks they have been assigned. Permissions should be reviewed and updated frequently to reduce the possibility of unauthorized access.
MFA(multi-factor authentication) - Use MFA to add an additional layer of protection. Enable MFA for all IAM users. MFA mandates that users supply an additional verification factor in addition to their standard password, such as a hardware token or a time-based one-time password (TOTP).
Regularly rotate access keys - Rotate access keys regularly. Access keys, which are used to communicate programmatically with AWS, are composed of an access key ID and a secret access key. To lessen the effects of potential key compromises, rotate these keys regularly.
Use IAM roles for EC2 instances - Assign IAM roles to EC2 instances rather than access keys. By using this method, managing and protecting access keys for specific instances is no longer necessary.
Enable AWS CloudTrail - AWS CloudTrail should be enabled since it offers thorough logs of API activity in your AWS account. Assist with audits, compliance, and security investigations by using CloudTrail to monitor and trace user behaviors.
Conclusion
Fine-grained access control and administration are provided by AWS IAM, which is essential for protecting your cloud infrastructure. Your AWS resources can be kept secure from unauthorized access and potential security risks if you follow the best practices recommended in this blog post. In order to maintain a stable and secure cloud environment and protect the data and resources of your company, IAM must be implemented properly.
IAM is only one piece of the security puzzle, so additional security measures like network security, encryption, and frequent security assessments should be used in addition to it. To safeguard your AWS resources in an ever-changing threat environment, be on the lookout, stay up to date with security best practices, and constantly evolve your security approach.
